
Hyper-volumetric DDoS (distributed denial of service) assaults within the first quarter of 2023 have shifted from counting on compromised IoT units to leveraging breached Digital Non-public Servers (VPS).
Based on web safety firm Cloudflare, the newer era of botnets progressively deserted the tactic of constructing giant swarms of individually weak IoT units and are actually shifting in direction of enslaving weak and misconfigured VPS servers utilizing leaked API credentials or recognized exploits.
This method helps the menace actors construct high-performance botnets simpler and infrequently faster, which could be as much as 5,000 occasions stronger than IoT-based botnets.
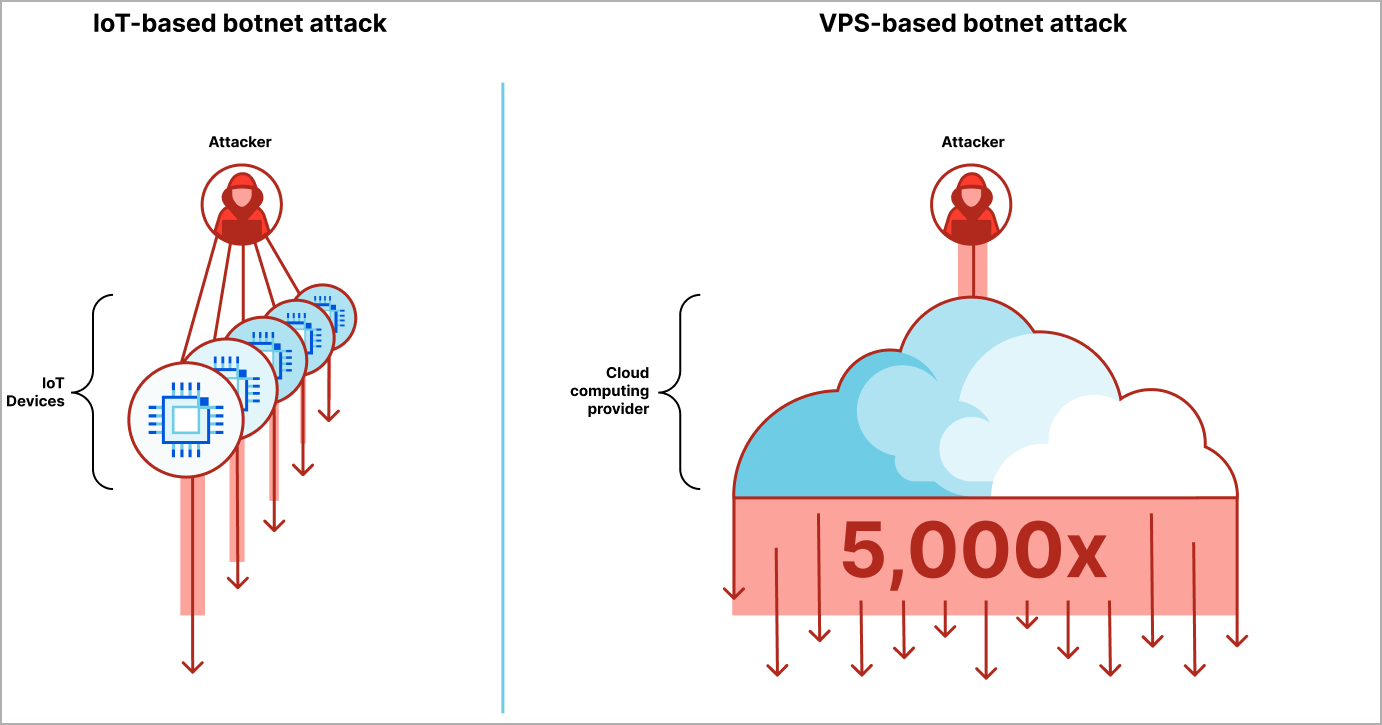
“The brand new era of botnets makes use of a fraction of the quantity of units, however every gadget is considerably stronger,” explains Cloudflare in the report.
“Cloud computing suppliers supply digital non-public servers to permit begin ups and companies to create performant purposes. The draw back is that it additionally permits attackers to create high-performance botnets that may be as a lot as 5,000x stronger.”
Cloudflare has been working with key cloud computing suppliers and companions to crack down on these rising VPS-based threats and says it has succeeded in taking down substantial parts of those novel botnets.
Q1 ’23 DDoS panorama
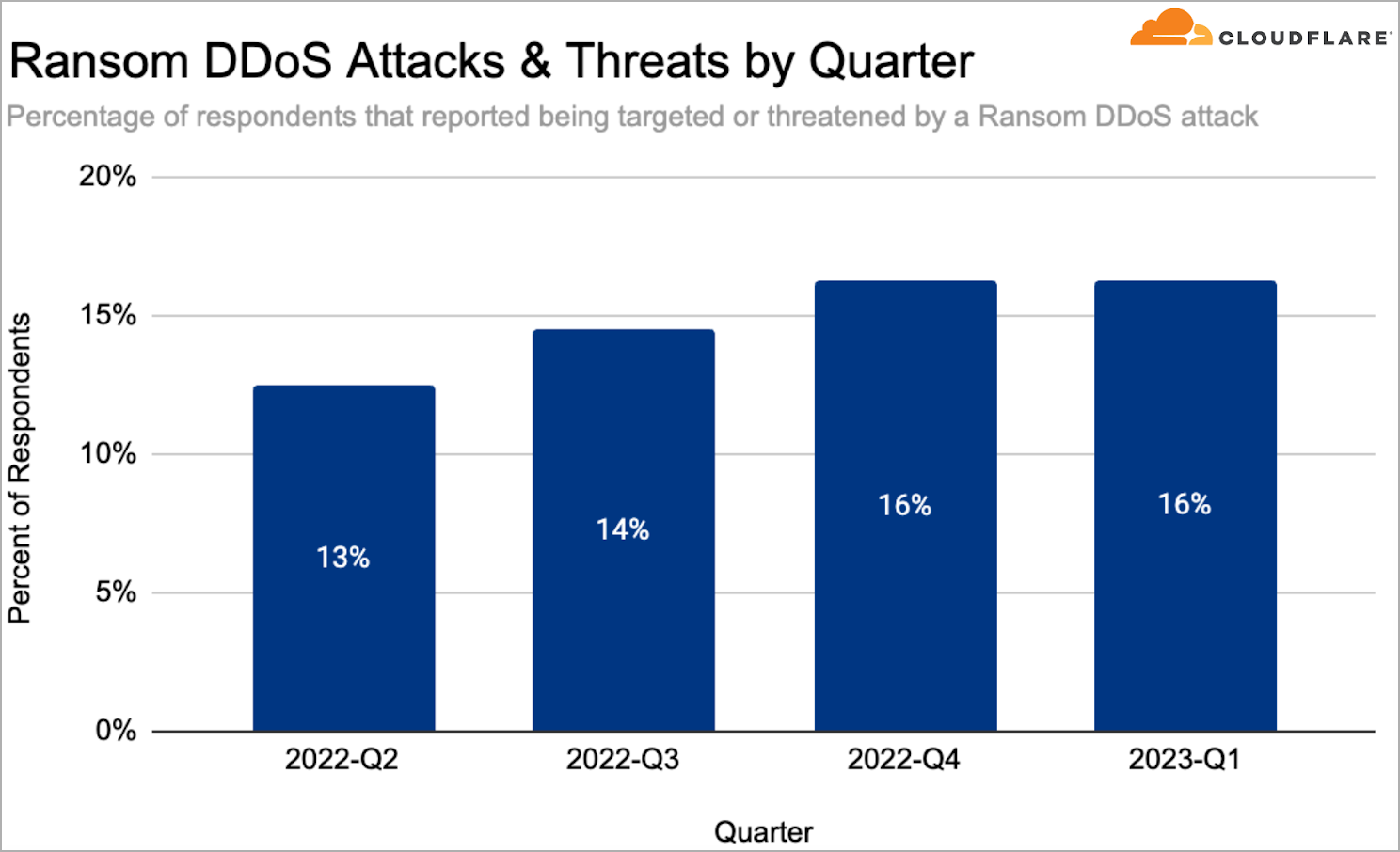
Typically, Cloudflare reviews regular DDoS exercise within the first quarter of the 12 months, with a notable 60% YoY improve within the ransom DDoS assaults, representing 16% of all recorded/reported DDoS assaults.
These extortion-based DDoS assaults trigger service outages to the goal by bombarding them with rubbish visitors and proceed indefinitely till the sufferer meets the attacker’s calls for.
Probably the most focused nation by DDoS assaults normally throughout Q1 ’23 was Israel, adopted by the USA, Canada, and Turkey. Web companies, advertising, software program, and gaming/playing have been essentially the most focused sectors.
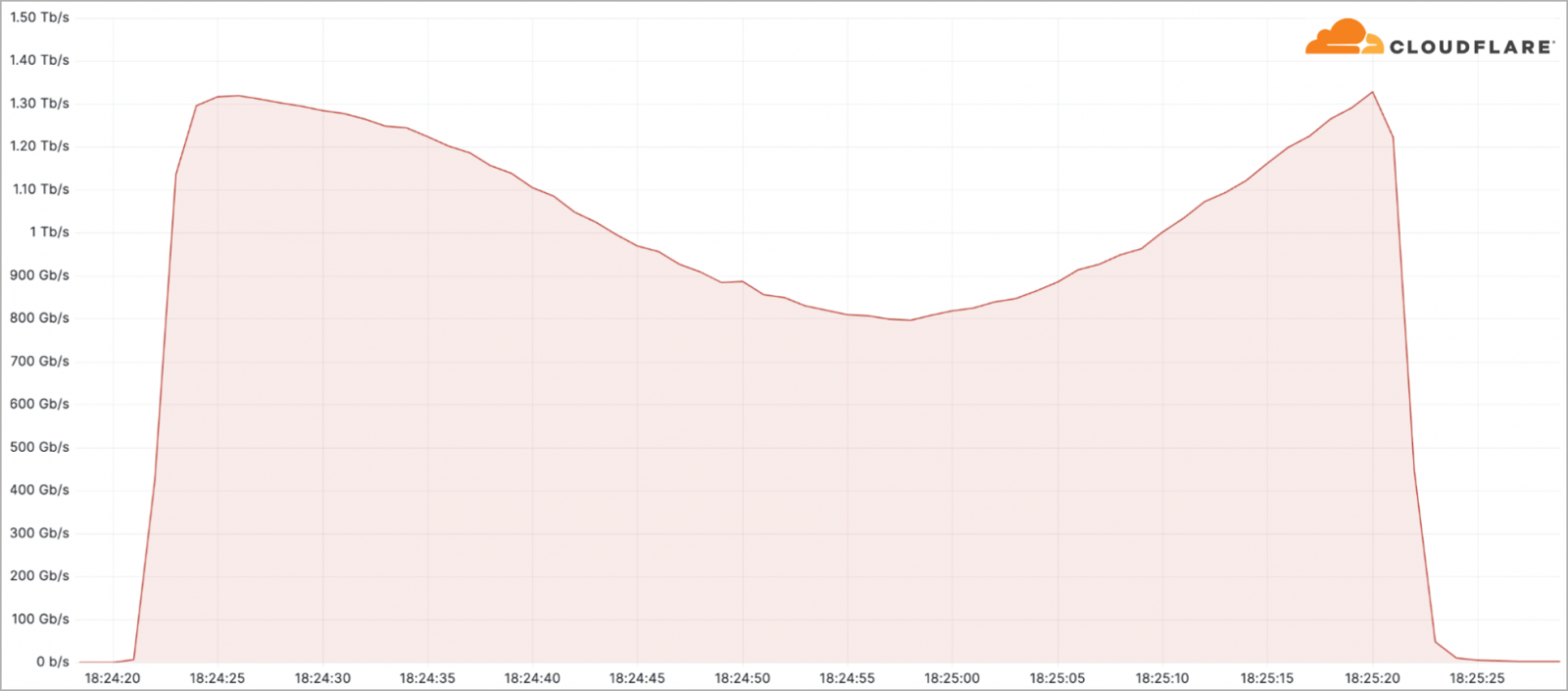
Probably the most vital assault seen by Cloudflare this quarter peaked above 71 million requests per second. One other notable incident was a 1.3 terabits per second DDoS assault concentrating on a telecommunications service supplier in South America.
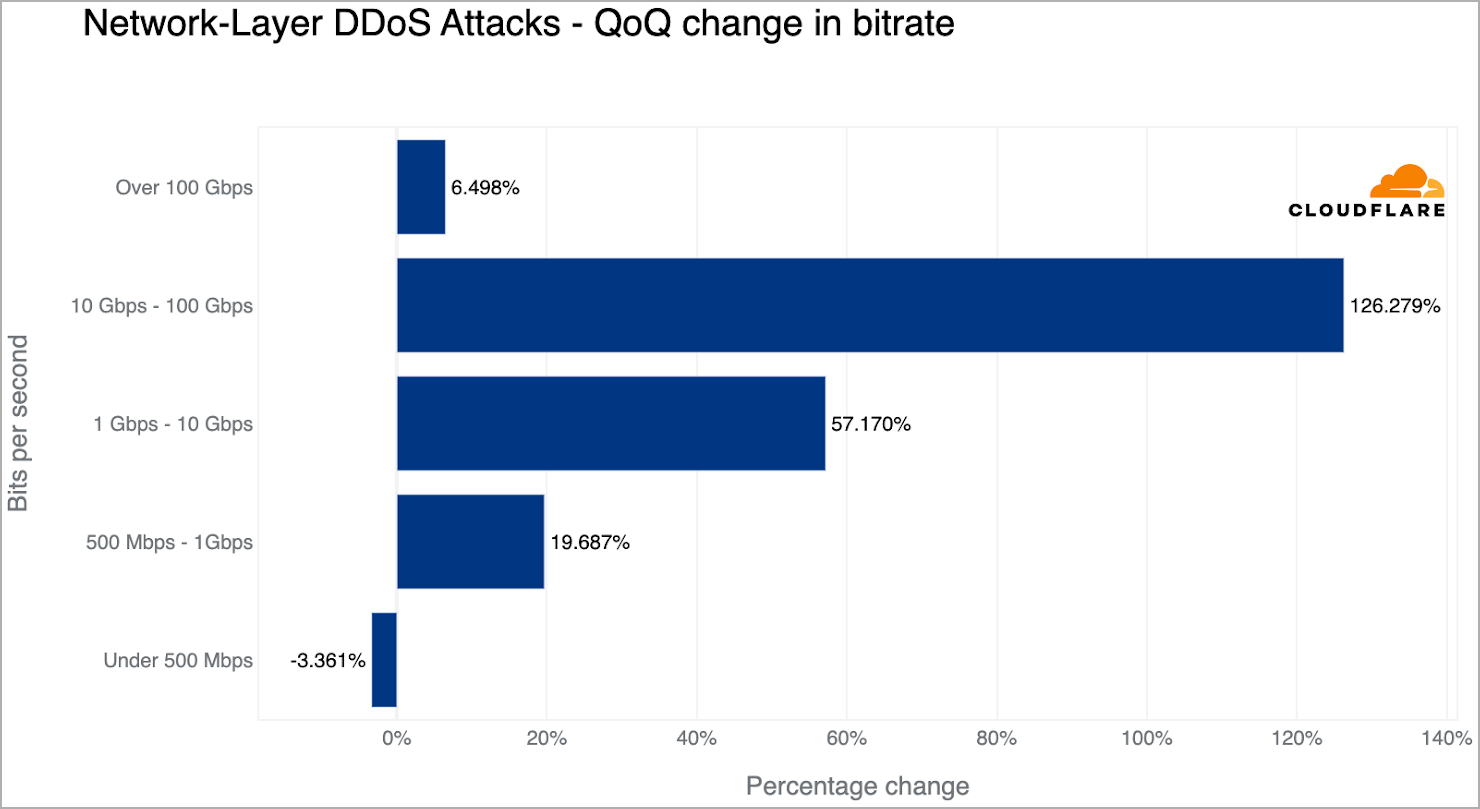
By way of the scale and length of the assaults, most of them (86.6%) lasted for below 10 minutes, whereas 91% didn’t exceed 500 Mbps.
Nevertheless, the variety of bigger assaults remains to be rising, with assaults surpassing 100 Gbps, recording an increase of about 6.5% in comparison with the earlier quarter.
Rising tendencies
DDoS assaults can manifest in some ways, and as defenses evolve to deal with them, attackers might devise new strategies or return to outdated ways that newer safety techniques might not prioritize anymore.
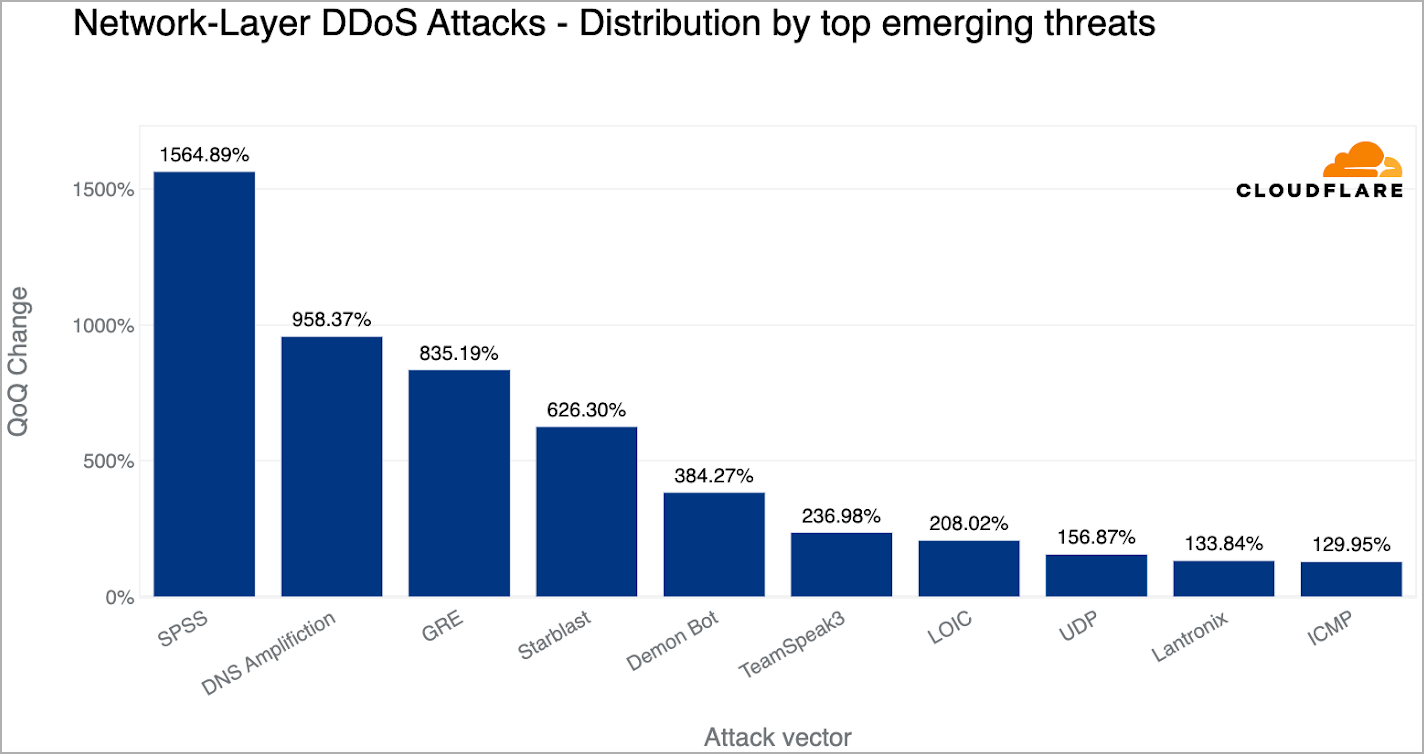
On this quarter, Cloudflare recorded the next rising tendencies:
- 1,565% QoQ improve in SPSS (statistical product and repair options) primarily based DDoS assaults. That is fueled by the exploitation of two flaws (CVE-2021-22731 and CVE-2021-38153) within the Sentinel RMS License Supervisor service, leveraged for launching reflection DDoS assaults.
- 958% QoQ rise in DNS amplification DDoS assaults, the place the attackers exploit DNS infrastructure flaws to generate giant quantities of visitors.
- 835% QoQ improve in GRE (generic routing encapsulation) primarily based DDoS assaults, the place attackers abuse the GRE protocol to flood the sufferer’s community with rubbish requests.
DDoS assaults in Q1 2023 present a pattern of accelerating in dimension and length, concentrating on a broad vary of industries. Due to this fact, efficient protection methods require automated detection and mitigation options.

