Analysis and improvement of quantum computer systems continues to develop at a speedy tempo. The U.S. authorities alone spent greater than $800 million on quantum info science (QIS) analysis in 2022. The promise of quantum computer systems is substantial – they are going to be capable to remedy sure issues which might be classically intractable, that means a standard pc can not full the calculations inside human-usable timescales. Given this computational energy, there may be rising dialogue surrounding the cyber threats quantum computer systems could pose sooner or later. For example, Alejandro Mayorkas, secretary of the Division of Homeland Safety, has recognized the transition to post-quantum encryption as a precedence to make sure cyber resilience. There may be little or no dialogue, nonetheless, on how we’ll defend quantum computer systems sooner or later. If quantum computer systems are to turn into such invaluable belongings, it’s affordable to undertaking that they are going to finally be the goal of malicious exercise.
I used to be lately invited to be a participant within the Workshop on Cybersecurity of Quantum Computing, co-sponsored by the Nationwide Science Basis (NSF) and The White Home Workplace of Science and Know-how Coverage, the place we examined the rising subject of cybersecurity for quantum computing. Whereas quantum computer systems are nonetheless nascent in some ways, it’s by no means too early to handle looming cybersecurity considerations. This put up will discover points associated to creating the self-discipline of cyber safety of quantum computing and description six areas of future analysis within the subject of quantum cybersecurity.
What’s Quantum Computing?
The widespread computer systems that most individuals use each day are constructed on the binary logic of bits, that are primarily based on 0 and 1 as represented by a binary bodily property, equivalent to whether or not circulation of electrical energy to a transistor is off or on. These conventional computer systems are usually known as classical computer systems when mentioned in relation to quantum computer systems. In distinction to the binary nature of classical computer systems, quantum computer systems use qubits, that are able to being in a superposition of two states on the identical time (i.e., representing each a 0 and 1 on the identical time). One analogy to understanding superposition is to think about flipping a coin. A classical pc can symbolize the coin as being heads or tails after the coin lands. A quantum pc, alternatively, can symbolize the coin as each heads and tails on the identical time whereas it’s nonetheless flipping within the air.
The potential of quantum computer systems is additional enriched by the property of entanglement, which permits distributed encoding of knowledge. Quantum entanglement permits qubits which might be separated, even by important distances, to work together with one another instantaneously. Entanglement happens when particles work together in such a manner that every particle’s quantum state can’t be described independently of the state of the others. That’s, the measured states of entangled particles are correlated such that measurement of state for a single particle permits probabilistic prediction of state for others. Think about the coin flipping instance from above; now think about that two cash are flipped on the identical time. As they’re flipping within the air, the states of every coin are correlated.
Collectively, quantum superposition and entanglement allow substantial computing energy. Think about {that a} 2-bit register in a classical pc can retailer solely one of 4 binary mixtures (00, 01, 10, or 11) at a given time, however a 2-qubit register in a quantum pc can retailer all 4 of those numbers concurrently. As extra qubits are added, this computational benefit of quantum computer systems over classical computer systems grows exponentially.
Cyber Threats to Quantum Computer systems
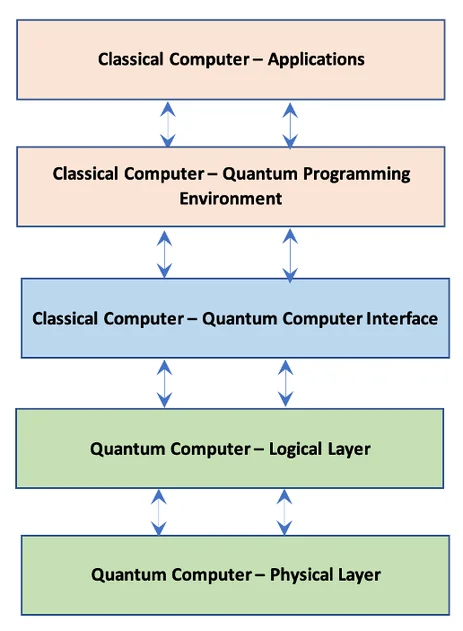
The present state of quantum pc methods is also known as the NISQ (noisy intermediate-scale quantum) period, characterised by quantum computer systems that supply reasonable computing energy and are nonetheless challenged by system constancy. Present quantum computer systems are unstable and unstable, with error-correction for quantum calculations nonetheless being addressed. Whereas researchers work to unravel these challenges, it’s obvious that within the near-term—and additional into the near-future—quantum computer systems will most definitely be used as co-processors in hybrid methods wherein classical computer systems will hand off mathematical calculations to the quantum pc as half of a bigger system workflow that also closely relies on classical computer systems. The diagram beneath reveals a notional idea of the parts for a quantum-classical hybrid comuting setting. Implementation particulars will range by quantum architectures, however related layers will exist in all quantum-classical hybrid computer systems.
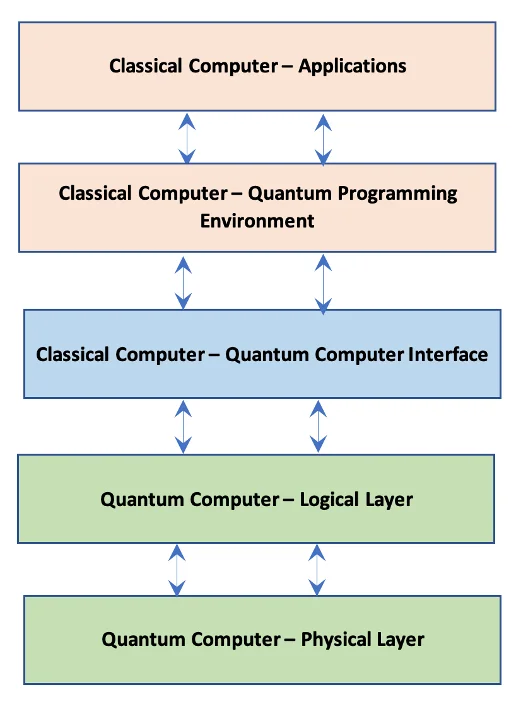
Determine 1: Notional Mannequin of Classical-Quantum Hybrid Laptop
Understanding how quantum computer systems can be built-in with classical computer systems is crucial to contemplating the cyber threats to quantum computer systems. The interface between classical and quantum computer systems within the hybrid computing environments typical of the NISQ-era is an space ripe for cybersecurity threats. This interface is actually the gateway between the classical and quantum environments, so it will probably function a conduit for recognized exploits of classical computer systems to traverse into quantum areas. In brief, there are already many recognized cyber assault methods for classical computer systems that may be leveraged to compromise a hybrid system.
One other assault vector stems from novel approaches for management and measurement of quantum gadgets that can be carried out in these interfaces. Utility-specific built-in circuits (ASICs), field-programmable gate arrays (FPGAs), digital-to-analogue converters (DACs), and different components of classical-quantum interfaces are being utilized in new methods. The present focus of analysis in designing these interfaces is on performance and efficiency, but safety considerations additionally should be addressed. Given the numerous recognized methods for compromising classical computer systems, it appears possible that assaults on quantum computer systems will originate in weaknesses in classical computer systems after which propagate to the quantum-classical interface.
Analysis sponsored by Microsoft Quantum Sydney outlines scalability points associated to present approaches for classical-quantum interfaces. The research highlighted challenges associated to I/O administration, warmth and energy dissipation, system footprint, noise and interference, and bandwidth. Whereas these points are introduced in relation to scalability, the identical points present avenues for assault. For example, attackers can leverage the warmth sensitivity to allow a denial-of-service assault or the proclivity for noise and interference to assault the integrity of operations. Our work in cybersecurity of classical computer systems has taught us that any system failure can present a gap to take advantage of a system.
Whereas securing the classical-quantum interface is a vital component in quantum cybersecurity, there are different areas to handle. For example, the output of quantum computing calculations can be way more invaluable to guard (and invaluable to steal) than most classical pc output, given the assets essential to carry out the calculations and derive the output. For example, a industrial pharmaceutical firm utilizing a quantum pc to unravel a fancy chemistry downside will contemplate that output fairly invaluable as a result of it could be laborious to breed and the end-product will containly extremely invaluable mental property.
Furthermore, the huge computing energy in quantum computer systems necessitates defending the quantum computational energy itself. That’s, not simply defending algorithms and their outputs but additionally detecting and defending towards hijacking of quantum computing functionality, in the identical manner a botnet assault hijacks classical computing energy. For instance, if adversaries shouldn’t have quantum computing energy of their very own, however wish to carry out a resource-intensive calculation, then they might attempt to get unauthorized entry to another person’s quantum functionality. Likewise, an adversary may wish to disrupt quantum-based computations solely to adversely affect the outcomes.
Lastly, a key distinction between quantum computer systems and classical computer systems is their sensitivity to temperature and the bodily world generally, which opens new vectors for denial-of-service-attacks. For example, the refrigeration necessities for a lot of quantum architectures opens an avenue to carry out a denial-of-service assault: disrupt the cooling for these architectures and their total operation may be halted. These are probably the most urgent of the numerous threats to quantum computer systems that the brand new self-discipline of quantum cybersecurity should tackle.”
6 Key Areas of Future Analysis in Quantum Cybersecurity
For the reason that design and structure of quantum computer systems remains to be an open space of analysis with many alternate options being explored, it’s untimely to give attention to particular vulnerabilities in particular methods. Researchers on this subject should first type an understanding of present and future threats to quantum computer systems to develop simpler protections. The previous part highlighted numerous threats to the confidentiality, integrity, and availability of quantum computer systems. This part higlights areas of analysis wanted to develop protections towards these threats.
For instance, one key space for future analysis is the event of capabilities for monitoring quantum computations. Quantum processing can’t be monitored in the identical ways in which system monitoring is completed for classical computer systems, which makes it laborious to each assess what algorithms quantum computer systems are operating and decide whether or not malicious processing is happening. This hole illustrates the necessity for creating a multi-layered instrumentation framework for quantum computer systems, which is likely one of the following six key areas for future quantum safety analysis we recognized within the Workshop on Cybersecurity of Quantum Computing:
- Constructing safe large-scale management methods. The dimensions of the classical computation concerned in supporting a large-scale quantum pc may be intensive. This help contains management methods and error correction, however it will probably additionally embrace monitoring for intrusions. Analysis is required on constructing safe classical management methods for quantum computer systems.
- Enabling distributed high-performance quantum computing. Classical high-performance computing methods are usually multi-tenant and distributed. Addressing the safety of multi-tenant and distributed quantum computer systems now can lay the muse for safer quantum computer systems after they obtain scale.
- Understanding assault vectors on various kinds of quantum computer systems. Deeper analysis on potential assault vectors for numerous quantum system fashions, equivalent to whether or not adversaries solely entry quantum gadgets by a consumer interface, is required to extra absolutely perceive tips on how to safe quantum computer systems.
- Creating formal strategies for secure and safe quantum computing methods. In computing, formal strategies confer with rigorous mathematical methods for specifying, creating, and verifying pc software program and {hardware}. Analysis is required on creating formal strategies for quantum computing to realize reliable quantum computing.
- Setting up a multi-layered instrumentation framework. Such a framework would enable security-relevant properties of quantum computer systems to be enforced or verified.
- Creating the mandatory instruments for service suppliers to confirm quantum algorithms. These instruments will allow the flexibility to confirm and management which algorithms are operating on a quantum pc, additionally helps be sure that a quantum pc is not going to carry out undesirable behaviors.
Whereas all these areas of analysis are vital for safeguarding quantum computer systems, the panorama of cyber threats will frequently change as quantum computing know-how evolves. All of the above areas ought to be researched and, in tandem, further areas for quantum cybersecurity analysis ought to be added as they turn into related. Methods for safeguarding classical computer systems, equivalent to risk modeling and contemplating methods to compromise the rules of the confidentiality, integrity, availability (CIA) triad, should be utilized frequently to quantum computer systems to find rising threats to analysis as this subject of quantum cybersecurity advances.
Securing Elevated Quantum Deployment Conclusion
As quantum computing turns into extra sensible, organizations should reply many questions on tips on how to leverage it for strategic use. Elevated quantum deployment will increase many technical questions on how information is ready and transferred to quantum computer systems, how algorithms are carried out in quantum computer systems, and the way quantum computing outcomes are returned and verified. With all these technical issues, an overarching query can be, How can this all be carried out securely? Right here on the CERT Division of the SEI, we have now an extended historical past of defending software program and computing methods. Furthermore, when the time involves make sensible, safe choices about using quantum computer systems, we’re able to welcome you to quantum cybersecurity!