An alarming variety of organizations aren’t correctly offboarding workers after they depart, particularly in regard to passwords. In a March PasswordManager.com survey of 1,000 U.S. employees who had entry to firm passwords at their earlier jobs, 47% admitted to utilizing them after leaving the corporate.
Safety groups needs to be terminating entry to all worker accounts, equivalent to e mail, cloud functions, and inner instruments, after workers depart. For accounts or providers the place a number of workers share passwords, these passwords needs to be rotated to make sure that the previous workers not have entry.
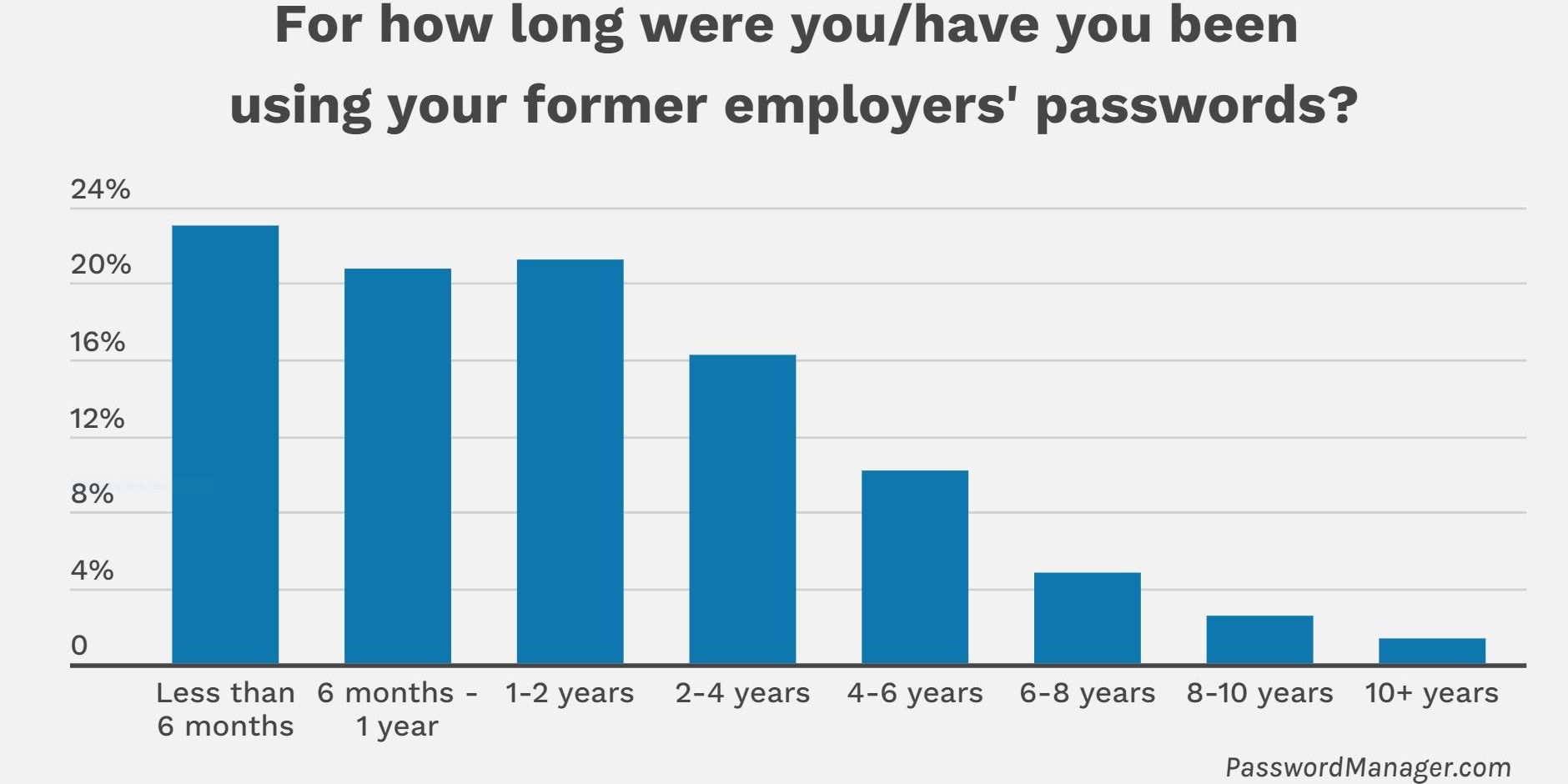
In keeping with the survey, 58% of respondents indicated they had been nonetheless in a position to make use of their former firm’s passwords after they left. One in three respondents mentioned they’d been utilizing the passwords for upwards of two years, which is a distressingly very long time for organizations not to concentrate on who’s accessing these accounts and providers.
“Ideally the corporate creates commonplace working procedures or constant schedules of updating passwords based mostly on criticality,” says Daniel Farber Huang, head of privateness and cybersecurity at PasswordManager.com.
When requested what they use the passwords for, 64% mentioned to entry their former e mail accounts and 44% to entry firm information. Although nearly all of the respondents, 56%, mentioned they had been accessing the accounts for private use, a regarding 10% mentioned they had been attempting to disrupt firm actions.
A survey from Past Identification in 2022 had related findings: Fifty-three % of worker respondents admitted to utilizing their entry to hurt their former employers, and 74% of enterprise leaders reported struggling damages from former workers who exploited their digital entry.