
The BianLian ransomware group has shifted its focus from encrypting its victims’ recordsdata to solely exfiltrating information discovered on compromised networks and utilizing them for extortion.
This operational growth in BianLian was reported by cybersecurity firm Redacted, who’ve seen indicators of the risk group making an attempt to craft their extortion expertise and enhance the strain on the victims.
BianLian is a ransomware operation that first appeared within the wild in July 2022, efficiently breaching a number of high-profile organizations.
In January 2023, Avast launched a free decryptor to assist victims get better recordsdata encrypted by the ransomware.
Current BianLian assaults
Redacted experiences that BianLian operators have saved their preliminary entry and lateral motion strategies the identical and proceed to deploy a customized Go-based backdoor that provides them distant entry on the compromised system, albeit a barely improved model of it.
The risk actors publish their victims in masked type as rapidly as 48 hours after the breach on their extortion website, giving them roughly ten days to pay the ransom.
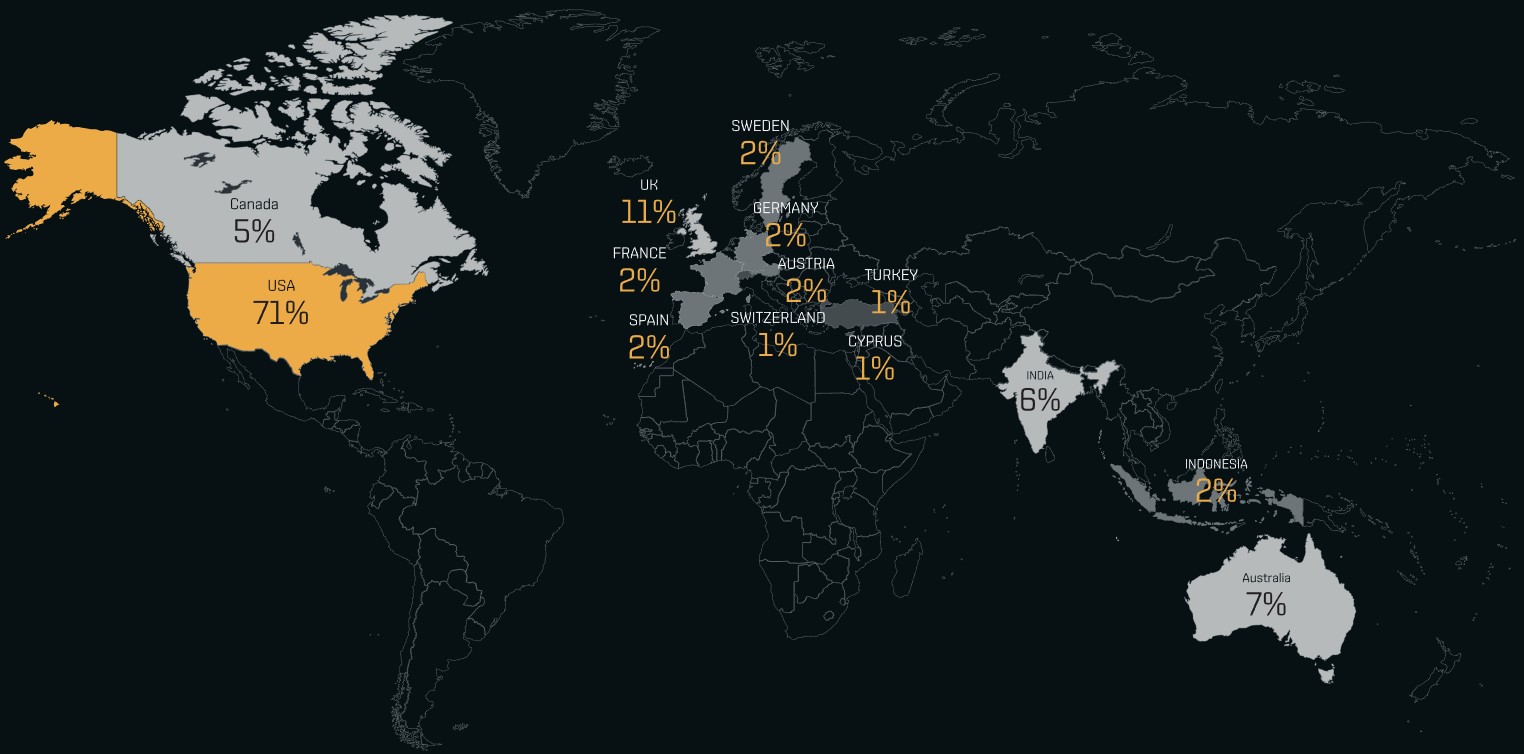
As of March 13, 2023, BianLian has listed a complete of 118 sufferer organizations on their extortion portal, with the overwhelming majority (71%) being U.S.-based corporations.
The primary distinction seen in current assaults is that BianLian makes an attempt to monetize its breaches with out encrypting the sufferer’s recordsdata. As a substitute, it now solely depends on threatening to leak the stolen information.
“The group guarantees that after they’re paid, they won’t leak the stolen information or in any other case disclose the very fact the sufferer group has suffered a breach. BianLian provides these assurances based mostly on the truth that their “enterprise” will depend on their status,” mentions Redacted within the report.
“In a number of situations, BianLian made reference to authorized and regulatory points a sufferer would face have been it to develop into public that the group had suffered a breach. The group has additionally gone as far as to incorporate particular references to the subsections of a number of legal guidelines and statutes.”
Redacted has discovered that in lots of instances, the regulation references made by BianLian operators have been relevant within the sufferer’s area, indicating that the risk actors are honing their extortion expertise by analyzing a sufferer’s authorized dangers to formulate robust arguments.
It’s unknown if BianLian deserted the encryption tactic as a result of Avast broke their encryptor or as a result of this occasion helped them notice they did not want that a part of the assault chain to extort victims into paying ransoms.
It must be talked about that when Avast launched its free decryptor, BianLian downplayed its significance, saying it could solely work on early “summer time 2022” variations of the ransomware and would corrupt recordsdata encrypted by all subsequent builds.
Extortion with out encryption
Encrypting recordsdata, information theft, and threatening to leak stolen recordsdata is called a “double extortion” tactic, which serves as a further type of coercion for ransomware gangs seeking to enhance strain on their victims.
Nevertheless, by the pure alternate between risk actors and victims, ransomware gangs realized that, in lots of instances, delicate information leak was a good stronger fee incentive for victims.
This gave delivery to encryption-less ransomware operations such because the late Babuk and SnapMC, and extortion operations that declare to not interact in file encryption themselves (or in any respect), like RansomHouse, Donut, and Karakurt.
Nonetheless, most ransomware teams proceed utilizing encryption payloads of their assaults, because the enterprise disruption brought on by encrypting gadgets places even larger strain on many victims.

