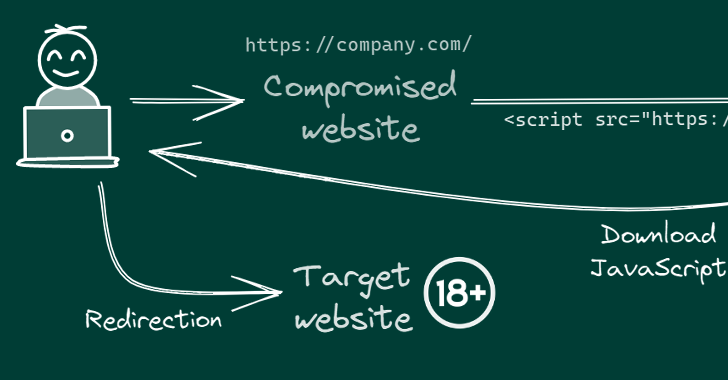
A widespread malicious cyber operation has hijacked hundreds of internet sites geared toward East Asian audiences to redirect guests to adult-themed content material since early September 2022.
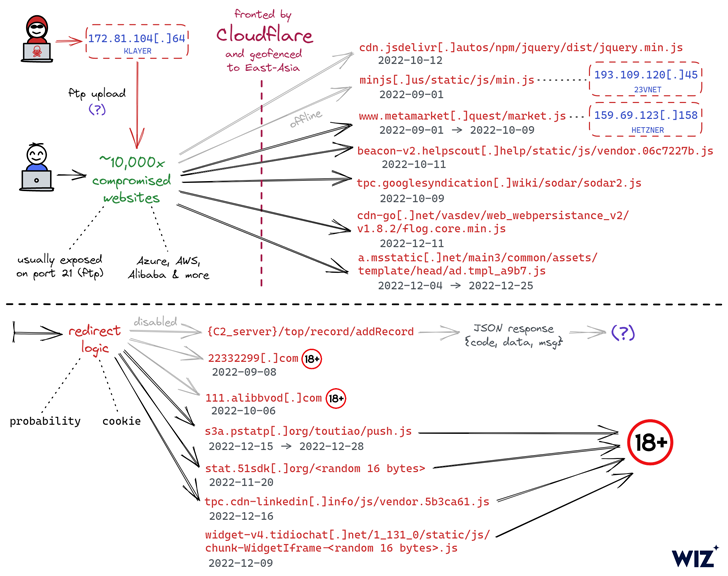
The continued marketing campaign entails injecting malicious JavaScript code to the hacked web sites, usually connecting to the goal internet server utilizing respectable FTP credentials the menace actor beforehand obtained through an unknown methodology.
“In lots of instances, these have been extremely safe auto-generated FTP credentials which the attacker was someway capable of purchase and leverage for web site hijacking,” Wiz stated in a report printed this month.
The truth that the breached web sites – owned by each small corporations and multinational firms – make the most of completely different tech stacks and internet hosting service suppliers has made it troublesome to hint a typical assault vector, the cloud safety firm famous.
That having stated, one of many frequent denominators between the web sites is {that a} majority of them are both hosted in China or hosted in a distinct nation however are primed for Chinese language customers.
What’s extra, the URLs internet hosting the rogue JavaScript code are geofenced to restrict its execution in sure East Asian nations.
There are additionally indications that the marketing campaign has set its sights on Android as nicely, with the redirection script main guests to playing web sites that urge them to put in an app (APK bundle identify “com.tyc9n1999co.coandroid“).
The id of the menace actor is unknown as but, and though their exact motives are but to be recognized, it’s suspected that the objective is to hold out advert fraud and search engine marketing manipulation, or alternatively, drive inorganic site visitors to those web sites.
Uncover the Hidden Risks of Third-Get together SaaS Apps
Are you conscious of the dangers related to third-party app entry to your organization’s SaaS apps? Be a part of our webinar to be taught in regards to the kinds of permissions being granted and how you can decrease danger.
One other notable facet of the assaults is the absence of phishing, internet skimming, or malware an infection.
“We stay uncertain as to how the menace actor has been gaining preliminary entry to so many web sites, and we’ve but to determine any vital commonalities between the impacted servers aside from their utilization of FTP,” researchers Amitai Cohen and Barak Sharoni stated.
“Though it is unlikely that the menace actor is utilizing a 0-day vulnerability given the apparently low sophistication of the assault, we won’t rule this out as an possibility.”