Tales from the SOC is a weblog collection that describes current real-world safety incident investigations carried out and reported by the AT&T SOC analyst group for AT&T Managed Prolonged Detection and Response prospects.
Govt abstract
As we transfer in direction of extra automation, we must always keep in mind the danger of over-automating, or at the least make a aware determination to simply accept the dangers. That is particularly vital in automating response actions, which left unchecked may wreak havoc with day-to-day enterprise operations.
Investigation
The alarm
One night after regular enterprise hours, an alarm got here in indicating a software program package deal trying to execute on a server was auto-mitigated by SentinelOne. The software program package deal was behaving in a method that was taken as trying to evade detection by the SentinelOne agent and subsequently rated as “Malicious” by the SentinelOne Synthetic Intelligence logic. Because the server on which the software program package deal was trying to execute had a “Defend” coverage utilized, the auto-mitigation steps for a dynamically detected “Malicious” score included killing and quarantining the method.
A “coverage” setting in SentinelOne is the outlined stage of automated response exercise the endpoint detection and response software (EDR) has permission to carry out for every grouping of belongings. Whereas a “Detect” coverage will create an alert that may be managed for post-investigation response actions, a coverage setting of “Defend” will take automated response actions. The intrusion stage of these automated response actions may be custom-made, however all of them carry out an automatic motion with out a individual wanting on the scenario first.
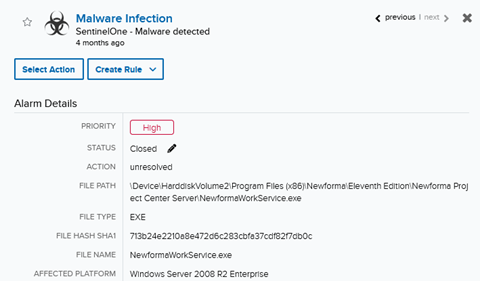
The beneath picture is for an alarm for malware which ended up being course of automation software program
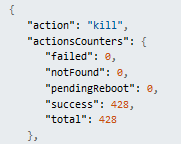
however nonetheless was automitigated (course of killed) by SentinelOne as proven within the log excerpt beneath.
The enterprise impression
The following morning, with enterprise hours again in full swing, the client reached out to us involved about the results of the automated response motion. The shopper said that the software program package deal is a crucial a part of their enterprise infrastructure and may by no means be stopped from executing. The software program had been operating on that very same server the prior a number of months, since coming into SOC monitoring.
The shopper questioned why after a number of months with the SentinelOne agent operating on the server did the agent instantly imagine the software program package deal was malicious. We weren’t ready the reply the query particularly because the decision-making behind figuring out and score a course of as “Malicious” versus “Suspicious” or benign is a proprietary logic.
What we may state is that any EDR resolution value its value will regularly replace indicator of compromise (IOC) signatures. Any worthwhile EDR resolution can even embody not solely static detection but additionally behavior-based dynamic detection. Within the case of SentinelOne, there’s the pre-execution habits evaluation that enables for course of termination pre-execution as effectively. And naturally, any software program package deal run on a server is topic to updates for safety, effectivity, or product function upgrades.
Taken as a complete, it means any endpoint being protected is a really dynamic battleground with the potential for an up to date software program package deal that didn’t set off IOC guidelines yesterday triggering tehm as we speak. Or a non-updated software program package deal might instantly be recognized as potently malicious resulting from up to date machine studying IOC habits evaluation. Keep in mind when JNDI calls had been thought-about benign?
Classes discovered
Simply as we study the CIA safety triad is a balancing act between confidentiality, integrity and availability, there’s a steadiness to be struck between using fast automated response actions and the slower reasoning of human analysis previous to response actions. An EDR resolution will instantly and infallibly perform the coverage which it has been programmed to implement, however in a ruthless trend. A human analysis will take longer, however it will probably contemplate prior historical past, the validity of the triggering IOCs in context, and the nuances of how choosing one response motion over one other may impression your general enterprise.
Automation, machine studying, synthetic intelligence, and the like have their place. Their advantages will little doubt enhance as know-how develops. However the human part will at all times be needed. The MXDR SOC and our prospects (being the people that we’re) should work collectively to outline the crucial belongings and enterprise processes that ought to by no means be touched by automated intrusion. We should additionally work collectively to seek out the house in your atmosphere the place these swift and ruthless automated response actions are a bonus. And it’s a very human determination to conclude how a lot threat we are able to tolerate in every implementation.