
Microsoft urged prospects at present to maintain their on-premises Change servers patched by making use of the most recent supported Cumulative Replace (CU) to have them all the time able to deploy an emergency safety replace.
Redmond says that the Change server replace course of is “simple” (one thing that many admins would possibly disagree with) and recommends all the time working the Change Server Well being Checker script after putting in updates.
This helps detect widespread configuration points identified to trigger efficiency points or points that may be fastened with a easy Change Atmosphere configuration change. If it finds any issues, the script offers hyperlinks to articles with step-by-step steering for any further handbook duties that should be carried out.
“To defend your Change servers towards assaults that exploit identified vulnerabilities, you should set up the most recent supported CU (as of this writing, CU12 for Change Server 2019, CU23 for Change Server 2016, and CU23 for Change Server 2013) and the most recent SU (as of this writing, the January 2023 SU),” The Change Workforce stated.
“Change Server CUs and SUs are cumulative, so that you solely want to put in the most recent out there one. You put in the most recent CU, then see if any SUs have been launched after the CU was launched. In that case, set up the newest (newest) SU.”
Microsoft additionally requested Change admins to supply data on how the Change Server replace course of may very well be improved through an “replace expertise survey.”
“The aim of this survey is to grasp your Change Server cumulative replace (CU) and safety replace (SU) experiences in order that we will search for methods to enhance the experiences and aid you preserve your servers updated,” the corporate says.
“The knowledge collected on this survey will likely be used solely by the Change Server engineering workforce at Microsoft and solely to enhance the replace experiences.”
Some menace actors’ targets when focusing on Change servers embrace getting access to delicate data inside customers’ mailboxes, the corporate’s tackle guide, which might assist make social engineering assaults more practical, and the organizations’ Lively Listing and linked cloud environments.
Sadly, Change servers are extremely sought-after targets, as evidenced by the FIN7 cybercrime group’s efforts to create a customized auto-attack platform dubbed Checkmarks particularly designed to assist breach Change servers.
FIN7’s new platform has already been used to breach the networks of 8,147 firms (most of them situated in the USA) after scanning greater than 1.8 million targets, in keeping with menace intel agency Prodaft.
Tens of 1000’s of Change servers ready to be secured
As we speak’s warning comes after Microsoft additionally requested admins to repeatedly patch on-prem Change servers after issuing emergency out-of-band safety updates to deal with the ProxyLogon vulnerabilities that have been exploited in assaults two months earlier than official patches have been launched.
At the least ten hacking teams have been utilizing ProxyLogon exploits in March 2021 for varied functions, one being a Chinese language-sponsored menace group tracked by Microsoft as Hafnium.
To indicate the large variety of organizations uncovered to such assaults, the Dutch Institute for Vulnerability Disclosure (DIVD) discovered 46,000 servers unpatched towards the ProxyLogon bugs one week after Microsoft launched safety updates.
Extra just lately, in November 2022, Microsoft patched one other set of Change bugs often called ProxyNotShell that enable privilege escalation and distant code execution on compromised servers two months after in-the-wild exploitation was first detected.
The proof-of-concept (PoC) exploit the attackers used to backdoor Change servers was launched on-line one week after ProxyNotShell safety updates have been issued.
Final however not least, CISA ordered federal companies to patch a Microsoft Change bug dubbed OWASSRF and abused by the Play ransomware gang as a zero-day to bypass ProxyNotShell URL rewrite mitigations on unpatched servers belonging to Texas-based cloud computing supplier Rackspace.
This additional reveals the significance of following Microsoft’s recommendation to deploy the most recent supported CUs on all on-prem Change servers since mitigation alone is not going to essentially defend towards motivated and well-resourced attackers as they solely present short-term safety.
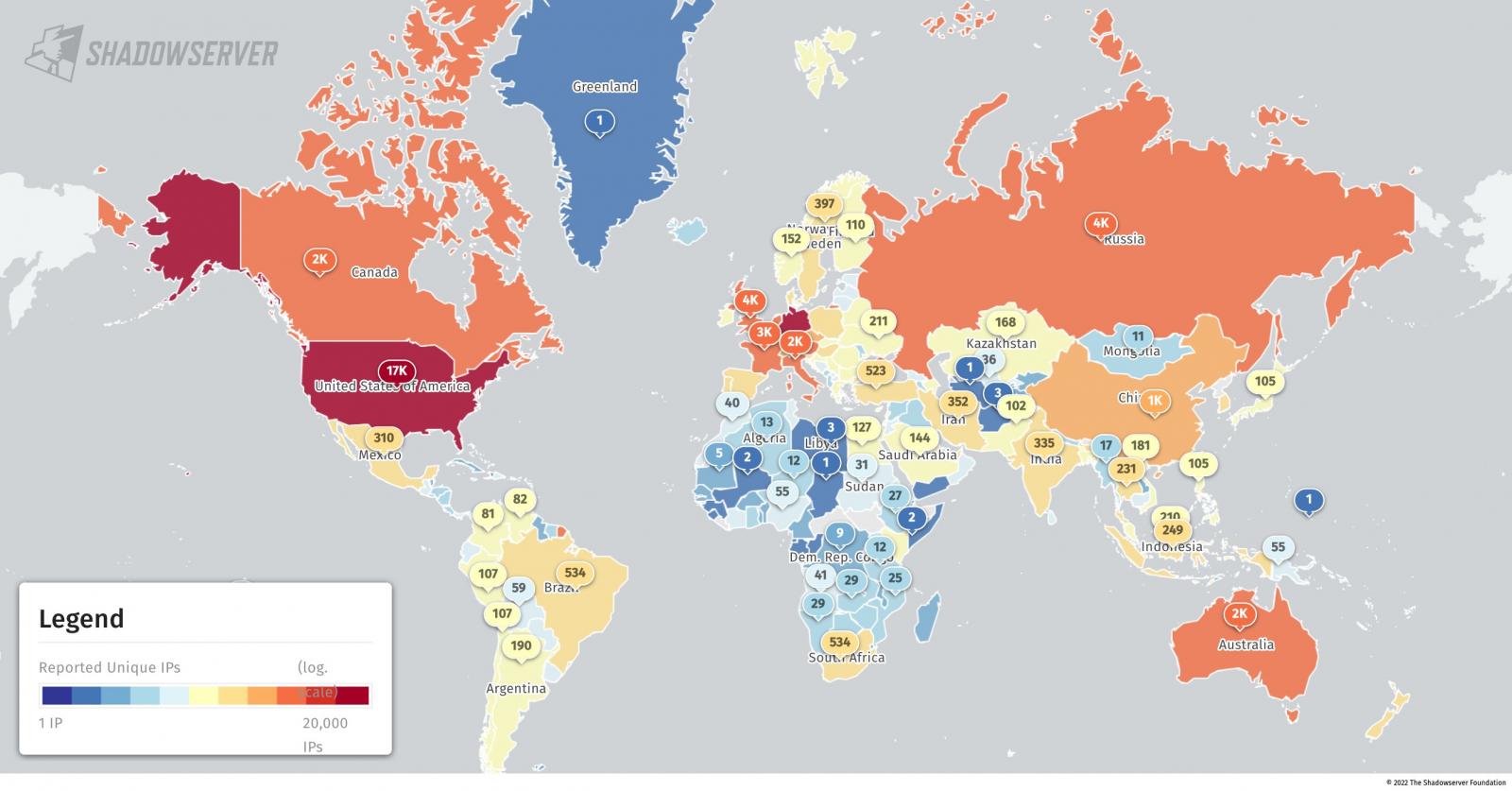
To place issues in perspective, earlier this month, safety researchers on the Shadowserver Basis discovered that over 60,000 Microsoft Change servers uncovered on-line are nonetheless weak to assaults leveraging ProxyNotShell exploits focusing on the CVE-2022-41082 distant code execution (RCE) vulnerability.
Making issues even worse, a search on Shodan reveals a substantial variety of Change servers uncovered on-line, with 1000’s nonetheless ready to be secured from assaults focusing on the ProxyShell and ProxyLogon flaws, among the most exploited vulnerabilities of 2021.

