
Malware operators have been more and more abusing the Google Advertisements platform to unfold malware to unsuspecting customers trying to find in style software program merchandise.
Among the many merchandise impersonated in these campaigns embody Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Workplace, Teamviewer, Thunderbird, and Courageous.
The menace actors the clone official web sites of the above initiatives and distribute trojanized variations of the software program when customers click on the obtain button.
Among the malware delivered to sufferer techniques this manner embody variants of Raccoon Stealer, a customized model of the Vidar Stealer, and the IcedID malware loader.
BleepingComputer has not too long ago reported on such campaigns, serving to to disclose a huge typosquatting marketing campaign that used over 200 domains impersonating software program initiatives. One other instance is a marketing campaign utilizing pretend MSI Afterburner portals to contaminate customers with the RedLine stealer.
Nonetheless, one lacking element was how customers had been uncovered to those web sites, a bit of data that has now develop into identified.
Two experiences from Guardio Labs and Development Micro clarify that these malicious web sites are promoted to a broader viewers by way of Google Advert campaigns.
Google Advertisements abuse
The Google Advertisements platform helps advertisers promote pages on Google Search, inserting them excessive within the record of outcomes as commercials, usually above the official web site of the challenge.
Which means that customers on the lookout for reliable software program on a browser with out an energetic advert blocker will see promotion first and are prone to click on on it as a result of it seems to be similar to the precise search outcome.
If Google detects that the touchdown web site is malicious, the marketing campaign is blocked, and the adverts are eliminated, so menace actors have to make use of a trick in that step to bypass Google’s automated checks.
In response to Guardio and Development Micro, the trick is to take the victims clicking on the advert to an irrelevant however benign web site created by the menace actor after which redirect them to a malicious web site impersonating the software program challenge.
.png)
“The second these “disguised” websites are being visited by focused guests the server instantly redirects them to the rogue web site and from there to the malicious payload,” explains Guardio Labs within the report.
“These rogue websites are virtually invisible to guests not reaching from the actual promotional circulate exhibiting up as benign, unrelated websites to crawlers, bots, occasional guests, and naturally for Google’s coverage enforcers” – Guardio Labs
The payload, which is available in ZIP or MSI kind, is downloaded from respected file-sharing and code-hosting companies resembling GitHub, Dropbox, or Discord’s CDN. This ensures that any anti-virus packages operating on the sufferer’s machine gained’t object to the obtain.
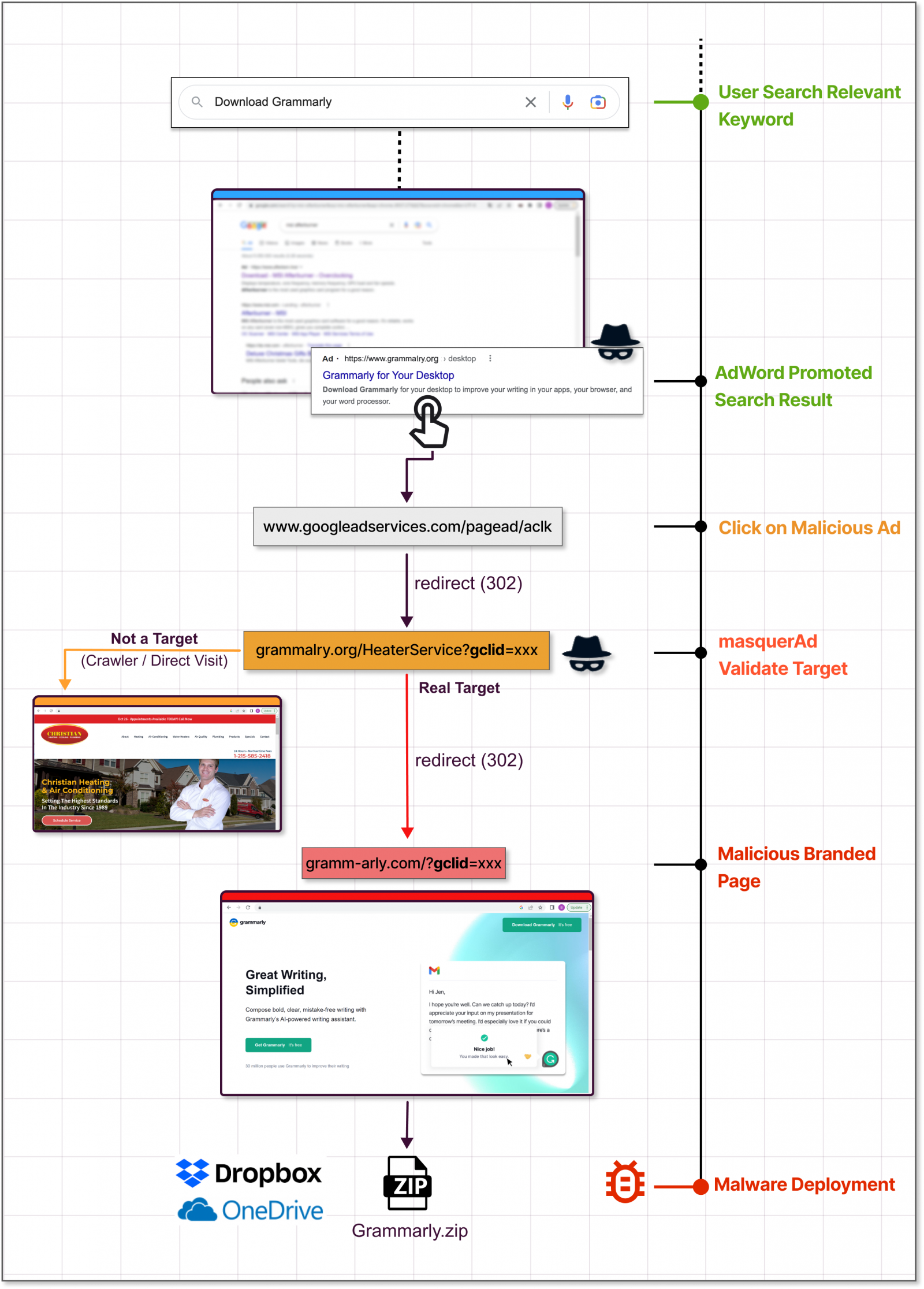
Guardio Labs says that in a marketing campaign they noticed in November, the menace actor lured customers with a trojanized model of Grammarly that delivered Raccoon Stealer.
The malware was bundled with the reliable software program. Customers would get what they downloaded and the malware would set up silently.
Development Micro’s report, which focuses on an IcedID marketing campaign, says the menace actors abuse the Keitaro Visitors Path System to detect if the web site customer is a researcher or a legitimate sufferer earlier than the redirection occurs. Abusing this TDS has been seen since 2019.
Keep away from dangerous downloads
Promoted search outcomes might be tough as they carry all of the indicators of legitimacy. The FBI has not too long ago issued a warning about the sort of advert marketing campaign, urging web customers to be very cautious.
One good option to block these campaigns is to activate an ad-blocker in your net browser, which filters out promoted outcomes from Google Search.
One other precaution can be to scroll down till you see the official area of the software program challenge you’re on the lookout for. If uncertain, the official area is listed on the software program’s Wikipedia web page.
For those who go to the web site of a selected software program challenge incessantly to supply updates, it’s higher to bookmark the URL and use that for direct entry.
A standard signal that the installer you’re about to obtain could be malicious is an irregular file dimension.
One other clear giveaway of foul play is the area of the obtain web site, which can resemble the official one however has swapped characters within the identify or a single incorrect letter, referred to as “typosquatting.”

