
A brand new assault methodology named COVID-bit makes use of electromagnetic waves to transmit knowledge from air-gapped programs, that are remoted from the web, over a distance of no less than two meters (6.5 ft), the place it is captured by a receiver.
The knowledge emanating from the remoted system may very well be picked up by a close-by smartphone or laptop computer, even when a wall separates the 2.
The COVID-bit assault was developed by Ben-Gurion College researcher Mordechai Guri, who has designed a number of strategies to steal delicate knowledge from air-gapped programs stealthily. Prior work consists of the “ETHERLED” and “SATAn” assaults.
Preliminary compromise
Bodily air-gapped programs are computer systems usually present in high-risk environments equivalent to vitality infrastructure, authorities, and weapon management items, so they’re remoted from the general public web and different networks for safety causes.
For a profitable assault on such programs, a rogue insider or an opportunist intruder should first plant custom-made malware on the goal computer systems via bodily entry to the air-gapped system or community.
As impractical and even far-fetched this will sound, such assaults have occurred, some examples being the Stuxnet worm in Iran’s uranium enrichment facility at Natanz, the Agent.BTZ that contaminated a U.S. navy base, and the Remsec modular backdoor that collected info from air-gapped authorities networks for over 5 years.
To transmit the info within the COVID-bit assault, the researchers created a malware program that regulates CPU load and core frequency in a selected method to make the facility provides on air-gapped computer systems emanate electromagnetic radiation on a low-frequency band (0 – 48 kHz).
“The first supply of electromagnetic radiation in SMPS is due to their inner design and switching traits,” Mordechai Guri explains within the technical paper.
“Within the conversion from AC-DC and DC-DC, the MOSFET switching parts turning on or off at particular frequencies create a sq. wave,” the researcher particulars.
The electromagnetic wave can carry a payload of uncooked knowledge, following a pressure of eight bits that signify the start of the transmission.
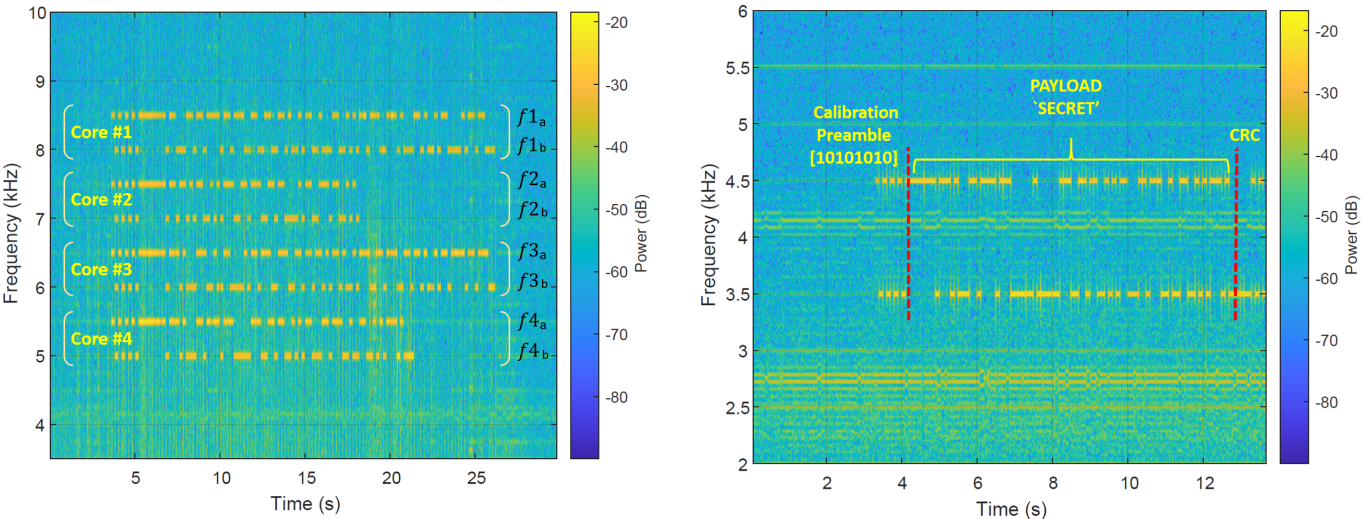
The receiver generally is a laptop computer or smartphone utilizing a small loop antenna related to the three.5mm audio jack, which might be simply spoofed within the type of headphones/earphones.
The smartphone can seize the transmission, apply a noise discount filter, demodulate the uncooked knowledge, and finally decode the key.

The outcomes
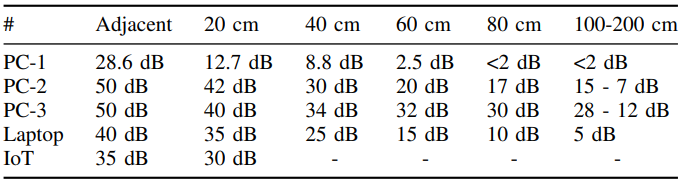
Guri examined three desktop PCs, a laptop computer, and a single-board laptop (Raspberry Pi 3) for varied bit charges, sustaining zero bit error fee for as much as 200 bps on PCs and the Raspberry Pi and as much as 100 bps for the laptop computer.
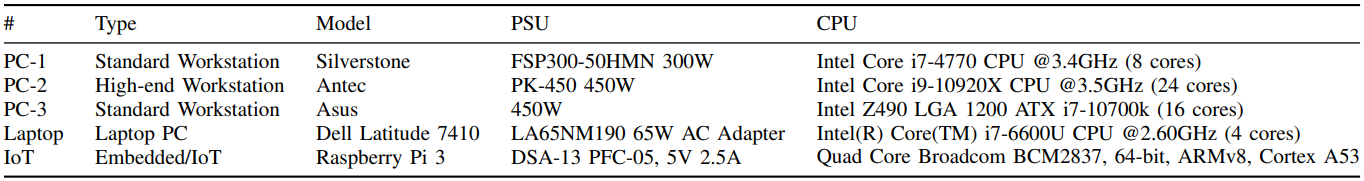
Laptops carry out worse as a result of their energy-saving profiles and extra energy-efficient CPU cores outcome of their PSUs not producing sturdy sufficient alerts.
The desktop PCs might attain a 500bps transmission fee for a bit error fee between 0.01% and 0.8% and 1,000 bps for a nonetheless acceptable bit error fee of as much as 1.78%.
The gap from the machine was restricted for the Raspberry Pi as a result of its weak energy provide, whereas the signal-to-noise ratio was additionally worse for the laptop computer because the testing probes moved additional away.
On the most examined transmission fee (1,000 bps), a 10KB file could be transmitted in 80 seconds, a 4096-bit RSA encryption key may very well be transmitted in as little as 4 seconds or as a lot as ten minutes, and the uncooked knowledge from one hour of keylogging could be despatched to the receiver in 20 seconds.
Reside keylogging would work in real-time, even for transmission charges as little as 5 bits per second.
.png)
The researcher additionally experimented with digital machines, discovering that interruptions in VM-exit traps to the hypervisor handler trigger a sign degradation between 2 dB and eight dB.
Defending towards COVID-bit
The simplest protection towards the COVID-bit assault could be to tightly prohibit entry to air-gapped gadgets to stop the set up of the required malware. Nonetheless, this doesn’t shield you from insider threats.
For this assault, the researchers advocate monitoring CPU core utilization and detecting suspicious loading patterns that don’t match the pc’s anticipated habits.
Nonetheless, this countermeasure comes with the caveat of getting many false positives and provides a knowledge processing overhead that reduces efficiency and will increase vitality consumption.
One other countermeasure could be to lock the CPU core frequency at a selected quantity, making the era of the data-carrying sign tougher, even when not stopping it totally.
This methodology has the disadvantage of diminished processor efficiency or excessive vitality waste, relying on the chosen lock frequency.

