We care deeply about privateness. We additionally know that belief is constructed by transparency. This weblog, and the technical paper reference inside, is an instance of that dedication: we describe an necessary new Android privateness infrastructure known as Non-public Compute Core (PCC).
A few of our most fun machine studying options use steady sensing information — info from the microphone, digital camera, and display. These options hold you protected, show you how to talk, and facilitate stronger connections with folks you care about. To unlock this new era of modern ideas, we constructed a specialised sandbox to privately course of and shield this information.
Android Non-public Compute Core
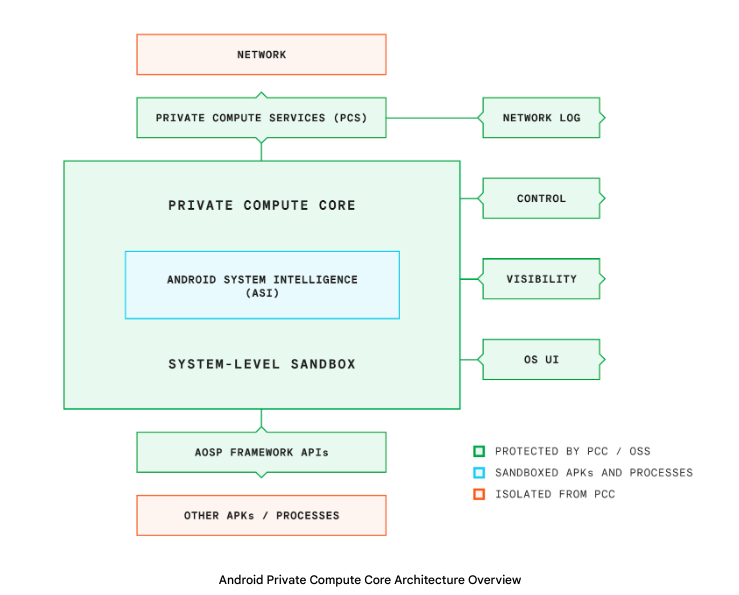
PCC is a safe, remoted information processing surroundings within the Android working system that offers you management of the info inside, resembling deciding if, how, and when it’s shared with others. This fashion, PCC can allow options like Reside Translate with out sharing steady sensing information with service suppliers, together with Google.
PCC is a part of Protected Computing, a toolkit of applied sciences that rework how, when, and the place information is processed to technically guarantee its privateness and security. For instance, by using cloud enclaves, edge processing, or end-to-end encryption we guarantee delicate information stays in unique management of the consumer.
How Non-public Compute Core works
PCC is designed to allow modern options whereas conserving the info wanted for them confidential from different subsystems. We do that through the use of methods resembling limiting Interprocess Communications (IPC) binds and utilizing remoted processes. These are included as a part of the Android Open Supply Undertaking and managed by publicly accessible surfaces, resembling Android framework APIs. For options that run inside PCC, steady sensing information is processed safely and seamlessly whereas conserving it confidential.
To remain helpful, any machine studying characteristic has to get higher over time. To maintain the fashions that energy PCC options updated, whereas nonetheless conserving the info non-public, we leverage federated studying and analytics. Community calls to enhance the efficiency of those fashions may be monitored utilizing Non-public Compute Providers.
Allow us to present you our work
The publicly-verifiable architectures in PCC show how we attempt to ship confidentiality and management, and do it in a approach that’s verifiable and visual to customers. Along with this weblog, we offer this transparency by means of public documentation and open-source code — we hope you may take a look under.
To clarify in much more element, we’ve revealed a technical whitepaper for researchers and members of the neighborhood. In it, we describe information protections in-depth, the processes and mechanisms we’ve constructed, and embody diagrams of the privateness constructions for steady sensing options.
Non-public Compute Providers was lately open-sourced as properly, and we invite our Android neighborhood to examine the code that controls the info administration and egress insurance policies. We hope you may look at and report again on PCC’s implementation, in order that our personal documentation just isn’t the one supply of study.
Our dedication to transparency
Being clear and engaged with customers, builders, researchers, and technologists around the globe is a part of what makes Android particular and, we predict, extra reliable. The paradigm of distributed belief, the place credibility is constructed up from verification by a number of trusted sources, continues to increase this core worth. Open sourcing the mechanisms for information safety and processes is one step in the direction of making privateness verifiable. The subsequent step is verification by the neighborhood — and we hope you may take part.
We’ll proceed sharing our progress and sit up for listening to suggestions from our customers and neighborhood on the evolution of Non-public Compute Core and information privateness at Google.