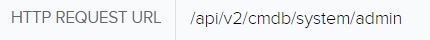Government abstract:
Fortinet’s latest vulnerability, CVE-2022-40684, permitting for authentication bypass to control admin SSH keys, unauthorized downloading of configuration information, and creating of tremendous admin accounts, has put an enormous goal on the backs of unpatched and uncovered Fortinet units.
An AT&T Managed Prolonged Detection and Response (MXDR) buyer was concerned in a real constructive compromise that was found by way of a risk hunt initiated off an Intrusion Safety System (IPS) alert from Fortinet. With coordination between buyer and MXDR and the shopper’s community and safety groups, the risk was remediated and contained, and the weak units had been patched.
Investigation
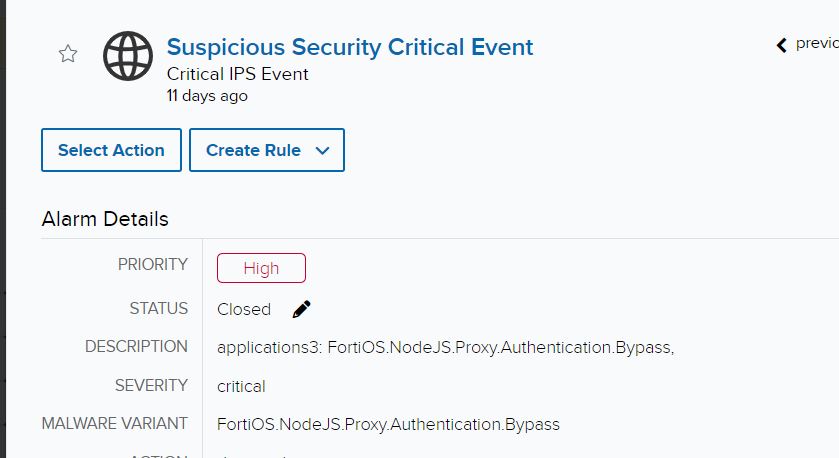
The preliminary investigation started throughout a tactical check-in with the shopper, who talked about an investigation concerning an IPS detection for 2 IP addresses that had been trying the authentication bypass exploit.
If we pivot to the occasion, we will see Fortinet created detections for probably unauthorized API requests to the cmdb filepath.
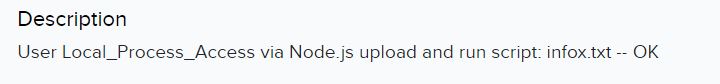
By Fortinet’s advisory on the vulnerability, we discovered that potential malicious exercise would originate from a person Local_Process_Access and would make the most of the Node.js or Report Runner interface. Stories point out that a number of the handlers for API connections examine sure circumstances, together with IP tackle being a loopback tackle and Person-Agent being both Report Runner or Node.js. Off that data, we’re capable of flip our consideration to potential true positives that weren’t picked up by the IPS. Doing a fast filter on the Local_Process_Access person produced some fascinating occasions:
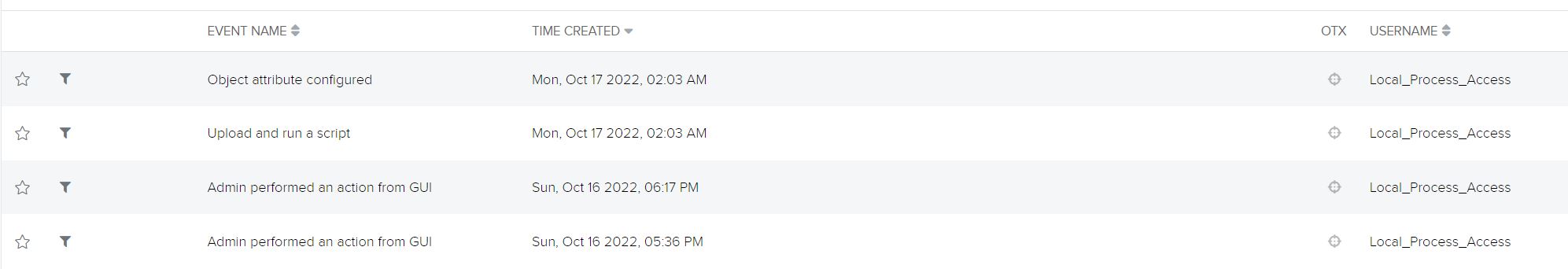
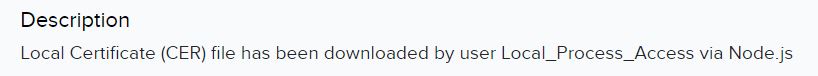
This doesn’t look good. The primary occasion we will see the attacker handle to efficiently obtain the Native Certificates:
This enables the attacker to see certificates data comparable to e mail tackle for the certificates proprietor, IP tackle of the Fortigate, firm identify, location the place the Fortigate was put in, and different delicate particulars. These native certificates a generated and offered to the Certificates Authority (CA) for surroundings belief.
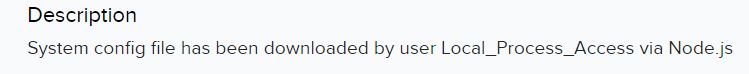
Shortly after, the attacker managed to obtain the system config of the Fortigate:
Lastly, a number of hours later they managed to add a script and run it to create a super_admin person:
That is the place the observable exercise ended from the Local_Process_User and newly created admin account. Remediation started at this level.
Response
After discovery of the administrator account, a community administrator was urgently contacted and was capable of take away the account. Throughout the remediation course of, the community administrator noticed that the administration port’s exterior interface had HTTPS open, which is probably going how the attacker gained the preliminary foothold. It’s believed the super_admin account that was created was for use as a backdoor in case the gadget was patched, as no exercise was seen from the account after creation. The script utilized by the attacker was not recovered, however following its add and execution it was doubtless simply used to create the admin account.
Significance of patching:
Fortinet did launch a patch the day this vulnerability was introduced, in addition to mitigation steps if patching was not instantly possible. One of many mitigation steps was to disable HTTPS/HTTP on the exterior dealing with administration interface if not wanted. The Fortinet Fortigate in query was the one gadget that had the administration interface open, and thus allowed the attacker a straightforward path to take advantage of the vulnerability.
Because of the detection of this exercise by way of risk searching by way of buyer logs, extra correlation logic was created for the USM Wherever platform to detect future compromises.