
A vital severity vulnerability in a WordPress plugin with greater than 90,000 installs can let attackers achieve distant code execution to totally compromise susceptible web sites.
Often known as Backup Migration, the plugin helps admins automate web site backups to native storage or a Google Drive account.
The safety bug (tracked as CVE-2023-6553 and rated with a 9.8/10 severity rating) was found by a group of bug hunters generally known as Nex Workforce, who reported it to WordPress safety agency Wordfence below a just lately launched bug bounty program.
It impacts all plugin variations as much as and together with Backup Migration 1.3.6, and malicious actors can exploit it in low-complexity assaults with out person interplay.
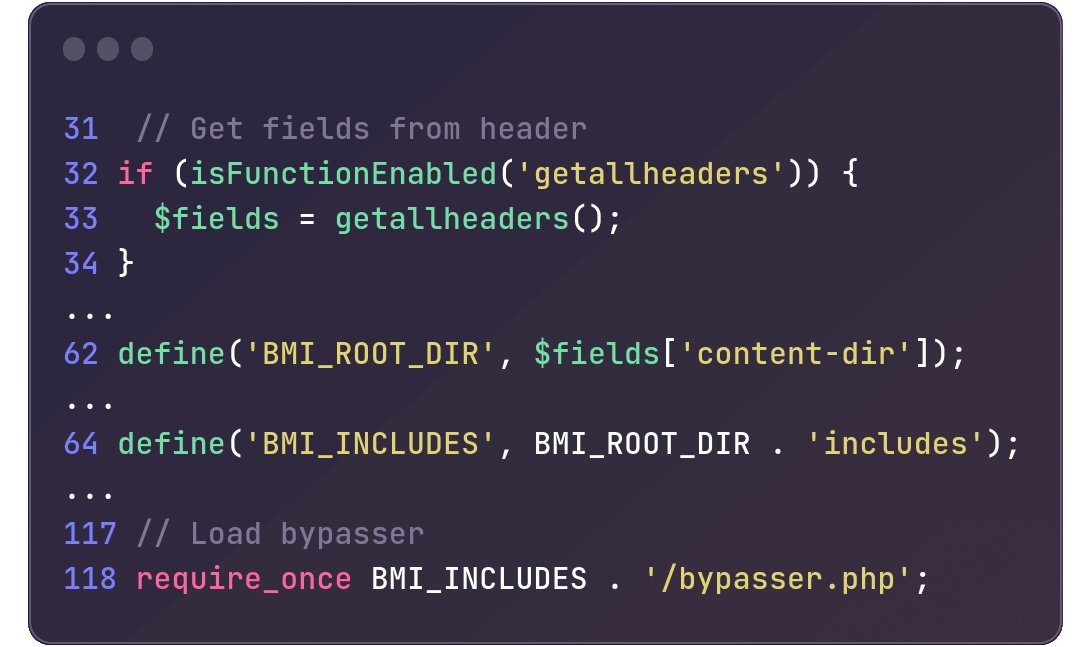
CVE-2023-6553 permits unauthenticated attackers to take over focused web sites by gaining distant code execution by PHP code injection through the /contains/backup-heart.php file.
“This is because of an attacker with the ability to management the values handed to an embrace, and subsequently leverage that to attain distant code execution. This makes it attainable for unauthenticated risk actors to simply execute code on the server,” Wordfence mentioned on Monday.
“By submitting a specially-crafted request, threat-actors can leverage this concern to incorporate arbitrary, malicious PHP code and execute arbitrary instructions on the underlying server within the safety context of the WordPress occasion.”
Within the /contains/backup-heart.php file utilized by the Backup Migration plugin, an try is made to include bypasser.php from the BMI_INCLUDES listing (outlined by merging BMI_ROOT_DIR with the contains string) at line 118.
Nonetheless, BMI_ROOT_DIR is outlined by the content-dir HTTP header discovered on line 62, thereby making BMI_ROOT_DIR topic to person management.
Patch launched inside hours
Wordfence reported the vital safety flaw to BackupBliss, the event group behind the Backup Migration plugin, on December 6, with the builders releasing a patch hours later.
Nonetheless, regardless of the discharge of the patched Backup Migration 1.3.8 plugin model on the day of the report, virtually 50,000 WordPress web sites utilizing a susceptible model nonetheless should be secured practically one week later, as WordPress.org org obtain stats present.
Admins are strongly suggested to safe their web sites in opposition to potential CVE-2023-6553 assaults, on condition that it is a vital vulnerability that unauthenticated malicious actors can exploit remotely.
WordPress directors are additionally being focused by a phishing marketing campaign making an attempt to trick them into putting in malicious plugins utilizing pretend WordPress safety advisories for a fictitious vulnerability tracked as CVE-2023-45124 as bait.
Final week, WordPress additionally mounted a Property Oriented Programming (POP) chain vulnerability that would enable attackers to achieve arbitrary PHP code execution below sure situations (when mixed with some plugins in multisite installations).

